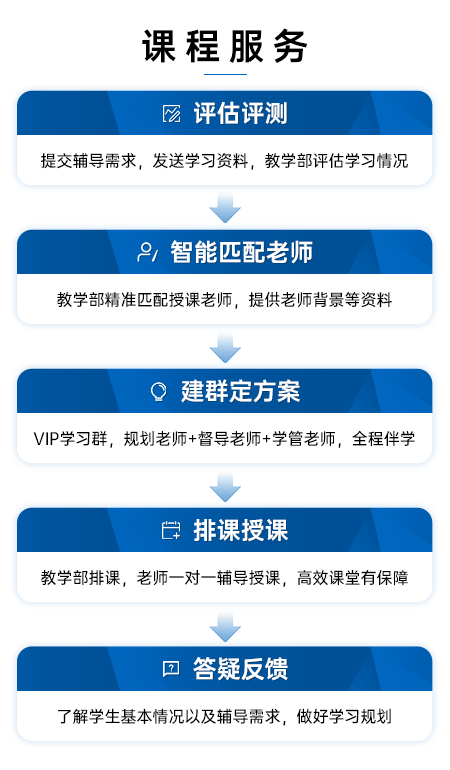
文章目录[隐藏]
中文赛题:网络强国?
情境
现代技术的奇迹使我们的世界越来越紧密地连接在一起。这种在线的互联性在提高全球生产力的同时,也让世界变得更小。然而,它也通过网络犯罪增加了我们个人和集体的脆弱性。网络犯罪因多种原因难以应对。许多网络安全事件跨越国界,导致调查和起诉这些犯罪的管辖权问题变得复杂。此外,许多机构(例如投资公司)不愿报告被黑客入侵的事件,而是倾向于悄悄支付赎金,而不是让客户和潜在客户知道他们成为了安全漏洞的受害者。为应对日益增长的网络犯罪成本和风险,许多国家制定了国家网络安全政策,这些政策可以在其政府网站上公开查阅。国际电信联盟(ITU)是联合国专注于信息和通信技术的专门机构,负责制定国际标准、促进国际合作以及开发评估工具,以帮助衡量全球和国家网络安全的现状。
要求
在本问题中,您被要求帮助识别可为基于数据的国家网络安全政策和法律的发展和优化提供信息的模式,重点是那些已被证明有效的政策和法律。为强有力的国家网络安全政策提出一个理论,并通过数据驱动的分析支持您的理论。在开发和验证您的理论时,您可能需要考虑以下内容:
- 网络犯罪在全球的分布情况如何?哪些国家是网络犯罪的高发目标?哪些国家的网络犯罪成功率高?哪些国家的网络犯罪被阻止?哪些国家的网络犯罪被报告或起诉?您是否发现了任何模式?
- 分析各国公开发布的国家安全政策,并将其与网络犯罪的分布情况进行比较。这种分析可以帮助您识别政策或法律中在应对网络犯罪(包括预防、起诉或其他缓解措施)方面特别有效(或特别无效)的部分。根据您的分析方法,政策采用的时间可能具有相关性。
- 哪些国家人口统计特征(例如互联网接入、财富、教育水平等)与您的网络犯罪分布分析相关?这些特征如何支持(或混淆)您的理论?
根据您收集和使用的数据的数量、质量和可靠性,分享任何国家政策制定者在依赖您的工作开发或优化其国家网络安全政策时应该考虑的局限性和/或问题。
您不需要创建新的网络安全衡量标准,因为已有如ITU的全球网络安全指数(GCI)等指标。[1]GCI根据五个支柱对每个国家的网络安全水平进行评分:法律、技术、组织、能力建设和合作。相反,您需要寻找国家网络安全政策和/或法律在其实施的国家背景下有效性的有意义模式。GCI或类似的现有研究可能对验证您的工作有用。此外,可能有用的资源包括收集网络犯罪数据的网站,特别是使用VERIS框架的网站,该框架尝试标准化网络犯罪数据的收集和报告,[2]包括VERIS社区数据库(VCDB)。[3]鼓励您查找其他数据来源,但请注意这些来源的真实性和完整性。
分享您的见解
利用您的工作为参加即将召开的ITU网络安全峰会的国家领导人(非技术性政策专家)创建一份一页的备忘录。该备忘录应提供您的工作的非技术性概述,包括目标和背景摘要、您的理论,以及对这群国家政策制定者最相关的发现。
您的 PDF 解决方案总页数不得超过25页,包括:
- 一页摘要页。
- 目录。
- 完整解决方案。
- 一封给交通官员的信(一页)。
- 参考文献列表。
- AI使用报告(如果使用不计入 25 页总限制)。
注意:完整的 MCM 提交文件没有特定的最低页数要求。您最多可使用 25 页来包含您的所有解决方案内容及其他补充信息(例如图纸、图表、计算和表格)。允许提交部分解决方案。我们允许谨慎使用 AI 工具(例如ChatGPT),但完成本问题并不一定需要使用 AI 工具。如果您选择使用生成式 AI 工具,必须遵循 COMAP的 AI使用政策。此政策要求您在解决方案文件的最后额外添加一份 AI 使用报告,不计入 25 页的总限制。
全新 MCM/ICM:在线提交流程
本文旨在协助和指导参加 MCM/ICM 的学生和顾问。在文章中,COMAP 提供了有关使用新在线提交页面的新在线提交流程的信息:
https://forms.comap.org/241335097294056
您需要团队的控制号、顾问 ID 号和问题选择才能完成提交。
术语表
(以下定义来源于多个国际组织的定义,包括ISO、ITU和INTERPOL。)
网络犯罪:网络犯罪包括利用数字设备和/或网络实施的广泛犯罪活动。
网络安全事件:单个(或一系列)不受欢迎或意外的计算机安全事件,这些事件具有显著可能性危害业务运营并威胁网络安全。
网络安全:网络安全是指可用于保护网络环境及组织和个人资产的工具、政策、安全概念、安全防护措施、指南、风险管理方法、行动、培训、最佳实践、保障和技术的集合。
Problem: Cyber Strong?
Background
More and more of our world has become connected through the wonders of modern technology. While this online connectedness has increased global productivity and made the world smaller, it has also increased our individual and collective vulnerability via cybercrime. Cybercrime is difficult to counter for a variety of reasons. Many cybersecurity incidents cross national borders, complicating issues of jurisdiction for both the investigation and the prosecution of these crimes. Additionally, many institutions, such as investment firms, are unwilling to report a hack, preferring to quietly pay a ransom demand than to let their clients and potential clients know that they were the victim of a security breach. To address the growing cost and risk of cybercrime, many countries have developed national cybersecurity policies, publicly available on their government websites. The International Telecommunication Union (ITU) is the specialized agency of the United Nations focused on information and communication technology; as such, they play a leading role in setting international standards, facilitating international cooperation, and developing assessments to help measure the status of global and national cybersecurity.
Requirements
In this problem, you are asked to help identify patterns that could inform the data-driven development and refinement of national cybersecurity policies and laws based on those that have demonstrated effectiveness. Develop a theory for what makes a strong national cybersecurity policy and present a data-driven analysis to support your theory. In developing and validating your theory, things you may wish to consider include:
- How is cybercrime distributed across the globe? Which countries are disproportionately high targets of cybercrimes, where are cybercrimes successful, where are cybercrimes thwarted, where are cybercrimes reported, where are cybercrimes prosecuted? Do you notice any patterns?
- As you explore the published national security policies of various countries and compare these with the distribution of cybercrimes, what patterns emerge that would help you identify parts of a policy or law that are particularly effective (or particularly ineffective) in addressing cybercrime (through prevention, prosecution, or other mitigation efforts)? Depending on your analytical approach, it may be relevant to consider when each policy was adopted.
- What national demographics (e.g., access to internet, wealth, education levels, etc.) correlate with your cybercrime distribution analysis? And how might these support (or conflate with) your theory?
Based on the quantity, quality, and reliability of the data you collected and used for your analysis, share any limitations and/or concerns that national policy makers should consider when relying on your work to develop and/or refine their national cybersecurity policies.
Your work should not seek to create a new measure of cybersecurity, as there are existing measures such as ITU's Global Cybersecurity Index (GCI),[1]which assigns a score to each country based on their level of cybersecurity as assessed through five pillars: legal, technical, organizational, capacity building, and cooperation. Instead, you have been asked to seek meaningful patterns in the effectiveness of national cybersecurity policies and/or laws with respect to the national contexts in which those policies were enacted. The GCI or similar existing research may be useful in validating your work. Additional resources that could be useful include websites that collect cybercrime data, particularly those leveraging the VERIS framework, which attempts to standardize how cybercrime data is collected and reported,[2]including the VERIS Community Database (VCDB).[3]You are encouraged to find other data sources but be mindful of the veracity and completeness of those sources.
Share Your Insights
Use your work to create a 1-page memo to country leaders (nontechnical policy experts) attending an upcoming ITU Summit on Cybersecurity. This memo should provide a nontechnical overview of your work, including a summary of the objective and context, your theory, and the most pressing findings that would be relevant to this audience of national policy-makers.
Your PDF solution of no more than 25 total pages should include:
- One-page Summary Sheet.
- Table of Contents.
- Your complete solution.
- One-page letter to the transportation officials.
- References list.
- AI Use Report (If used does not count toward the 25-page limit.)
Note: There is no specific required minimum page length for a complete MCM submission. You may use up to 25 total pages for all your solution work and any additional information you want to include (for example: drawings, diagrams, calculations, tables). Partial solutions are accepted. We permit the careful use of AI such as ChatGPT, although it is not necessary to create a solution to this problem. If you choose to utilize a generative AI, you must follow the COMAP AI use policy. This will result in an additional AI use report that you must add to the end of your PDF solution file and does not count toward the 25 total page limit for your solution.
NEW MCM/ICM: Online Submission Process
The purpose of this article is to assist and guide students and advisors participating in MCM/ICM. In the article, COMAP, provides information about the new online submission process using the new online submission page:
https://forms.comap.org/241335097294056
You will need your team's control number, advisor id number and your problem choice to complete your submission.
Glossary
(The following definitions are derived from definitions provided by multiple International Organizations, including ISO, ITU, and INTERPOL.)
Cybercrime: Cybercrime encompasses a wide range of criminal activities that are carried out using digital devices and/or networks.
Cybersecurity Incident: A single (or a series of) unwanted or unexpected computer security events that have a significant probability of compromising business operations and threatening cybersecurity.
Cybersecurity: Cybersecurity is the collection of tools, policies, security concepts, security safeguards, guidelines, risk management approaches, actions, training, best practices, assurance and technologies that can be used to protect the cyber environment as well as organizational and individual assets.
参考资料[1]
https://www.itu.int/epublications/publication/global-cybersecurity-index-2024
[2]
https://verisframework.org/index.html
[3]https://verisframework.org/vcdb.html